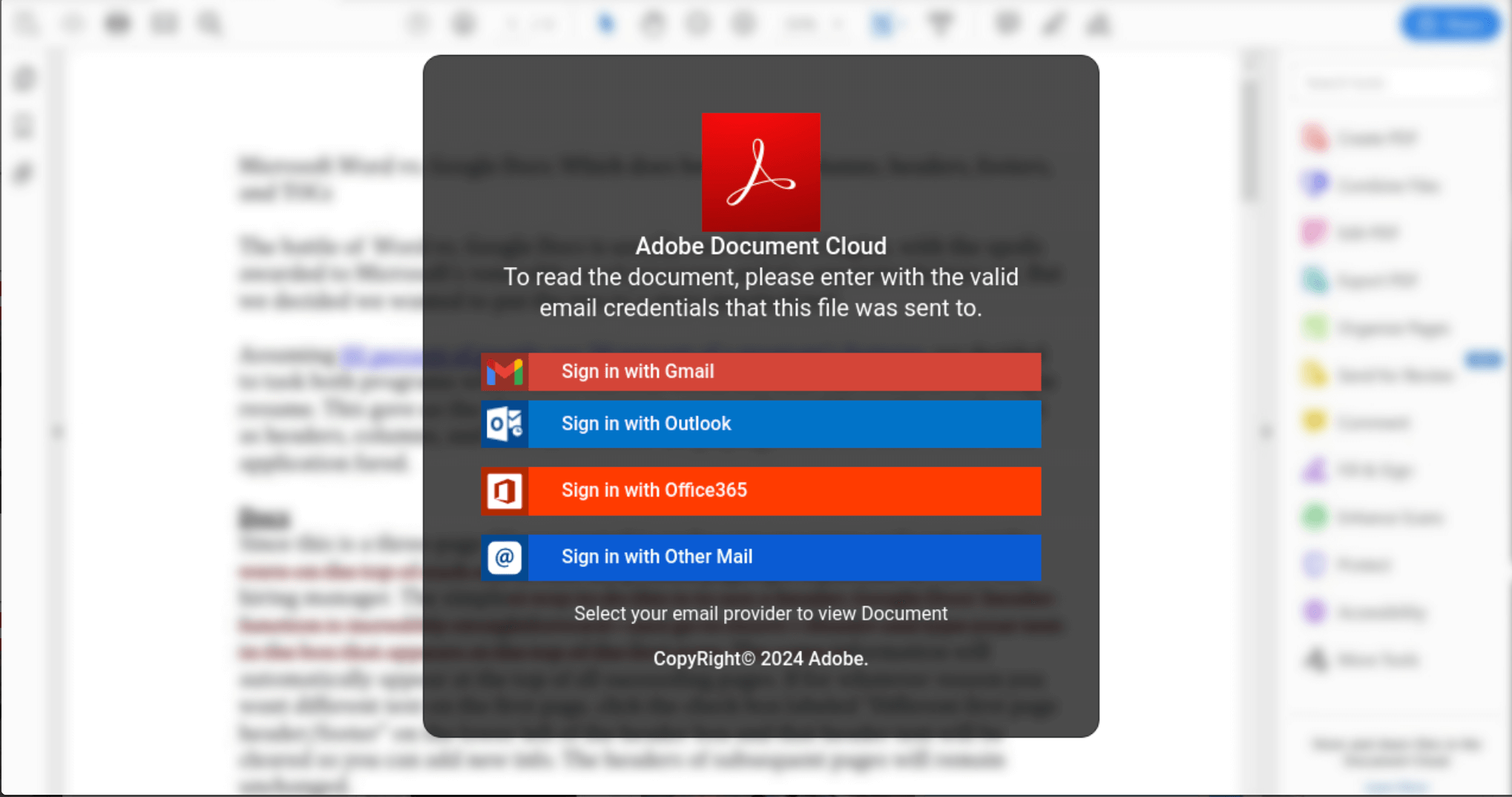
Credential stealing emails typically include malicious links that are specifically crafted to capture login credentials or solicit sensitive personal information. These emails often mimic legitimate communications from reputable sources to deceive recipients into providing their usernames, passwords, or other private data. The end goal for attackers is to gain unauthorized access to accounts or sensitive systems.
Due to our recent upgrade in our platform we here by request that you update your account immediately.
Kindly click the link below to download the account update form and complete the required information.
Failure to complete this update will result in account suspension.
Download Form
Thank you for choosing our services.
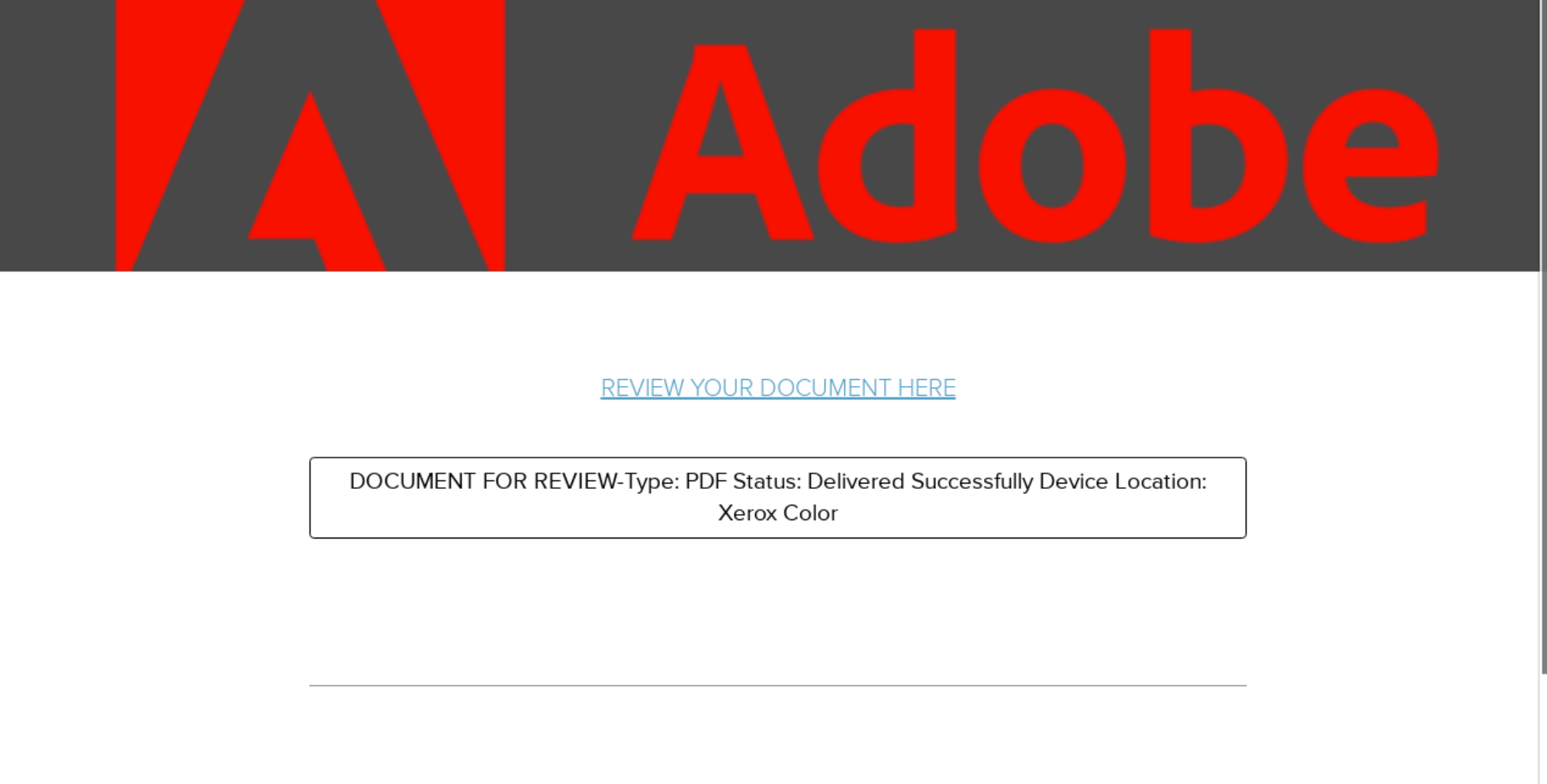
Fraudulent website phishing emails are deceptive messages that employ social engineering tactics to trap recipients in fraudulent schemes. Typically, these emails contain compelling messages crafted to lure users to click on a link. These actions redirect users to scam websites expertly designed to execute a range of online frauds, including gift scams, shipment scams, and Bitcoin scams. Each scam aims to manipulate users into divulging personal information or making financial transactions under false pretenses.
This is Adam from the Apple customer success team. Thanks for being a valuable customer. We would like to offer you an iPhone 15 Pro.
This is a time-sensitive offer. To take advantage of this exclusive deal, please click below to start the claim process as soon as possible.
Claim Now
Thanks
Adam
Apple Customer Success team
Technical Support Scam phishing emails use fear tactics by falsely alerting users to virus infections on their computers through email links that lead to deceptive websites. These sites urge users to take immediate action by calling a "technical support" number and connecting them to scammers pretending to be technicians. Once they gain the user's trust and remote access to the computer, these fraudsters can install malware, steal sensitive data, or alter system settings.
This is Lisa from Microsoft support. Your system has reported the presence of multiple-type viruses during the recent update. It's crucial to remove these viruses immediately to prevent any further damage to your system.
Please click the link below to start the troubleshooting session with our technical support team.
Contact Support
Thanks
Lisa
Microsoft Technical Support team

Rogueware emails are deceptive phishing schemes that lure recipients into downloading dangerous software. These emails usually include links leading to websites loaded with harmful binaries like spyware, malware, or rogue browser extensions. Crafted with social engineering tactics, the content of these emails is designed to entice users to click on the links and download the malicious software. The primary objectives of rogueware emails are to steal personal information, secure unauthorized access to computer systems, or recruit devices into botnets for illicit activities.
As part of a promotion, we would like to offer you a free copy of our VPN service. Please follow the link below to download and install a free copy of our entire software suite.
Browse Safe!
Download Instructions
Thanks
Sales Department
Nortron
QR phishing, also known as Quishing, is a deceptive tactic where cybercriminals embed malicious QR codes inside email body or attachments. Scanning these codes leads users to fraudulent websites that closely resemble legitimate ones. The purpose of these sites is to deceive individuals into submitting sensitive data such as login credentials, personal information, or financial details.
I am sending the project contract for your perusal. Please scan the QR code below to login to our portal to review the project details.
Kindly review & get back to me.
Regards